Thanks for coming back for our deep dive on the Center for Internet Security controls for small business. This week we’ll look at CIS Control #7: Continuous Vulnerability Management – and detail some practical steps you can take to secure and protect your business. Let’s dive in!
Continuous vulnerability management is a critical aspect of cybersecurity that many small businesses overlook. Have you ever put off updating your software because it seemed inconvenient? Or maybe you’ve discovered a security flaw but didn’t address it immediately? If so, you’re not alone, but this approach leaves your business exposed to potential threats.
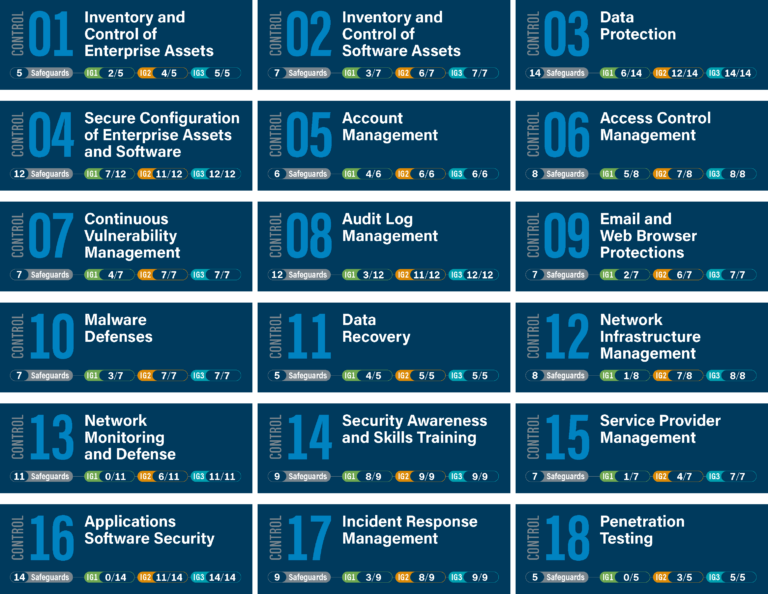
What is CIS Control 7?
CIS Control 7 focuses on continuously assessing, tracking, and remediating vulnerabilities in your business’s digital assets. Think of it as a constant health check-up for your IT infrastructure – identifying weaknesses before they can be exploited.
The full verbiage from CIS: Develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and minimize the window of opportunity for attackers.
Why should we worry about this?
Keeping your business safe online is an ongoing job because cyber threats are always changing. If we don’t fix these weak spots quickly, it’s like leaving our front door unlocked – anyone could walk in. By regularly checking for these weak spots and fixing them right away, we can do a much better job of protecting our business’s computer systems and data. Think of it as constantly patrolling your property to make sure all the doors and windows are secure.
Implementing CIS Control 7 in Your Small Business
Fear not! There are some practical steps you can take to identify where you might be vulnerable and take measures to keep cyberattackers out of your business:
- Know What You Have: Keep a list of all your computers, software, and other digital tools so you know what needs protecting.
- Check for Weak Spots Regularly: Use tools that automatically scan your systems to find any security issues or weaknesses.
- Focus on the Big Problems First: When issues are found, figure out which ones could cause the most harm and fix those first.
- Fix Problems Quickly: Have a clear plan to address security issues as soon as they come up.
- Keep Software Updated: Use tools that automatically install updates and security fixes for your programs and systems.
- Stay Alert: Set up tools that watch for new threats in real time so you can act fast if something risky shows up.
- Have a Backup Plan: Make sure you have a process in place to respond quickly if a serious issue is found, so you can limit any damage.
Remember, in cybersecurity, you’re only as strong as your weakest link. Don’t let unaddressed vulnerabilities be that weak link. Start implementing CIS Control 7 today – your organization’s future may depend on it.
Have questions about implementing CIS Control 7 in your business? Drop a comment below or get in touch with any questions you might have.
You can read more about the CIS Security Controls framework at the Center for Internet Security website and find all 18 controls listed there.
Stay secure, stay successful!
Michael @ MZ DATA
Long Beach, CA